SECURE DIGITAL COMUNICATIONS
Since the rise of the internet people around the world found themselves with the opportunity to communicate with anyone at any time. Any message is transformed into a binary string and sent through different means of telecommunication (satellite, fibre, etc…) over the internet network. However, this powerful technology comes at a price. Whoever would tamper the communication link would find himself able to read whatever message is passing through it and if confidential or sensitive information is needed to be transfer this would imply an impossibility to use such a link. For this reason, each message sent in the network must be encoded so that only the transmitter and receiver of the information will be able to read it.
How to encode a message is the topic of interest of Cryptography, the art of hiding a message, that has been around for millennia. Nowadays, the most common encoding schemes are the so called public key schemes, where a public key is broadcasted by a service provider and anyone with it could encode a message, however the only one able to read it is the possessor of the private key. Meaning that the communication can be left secure if the private key is kept secret. These protocols, however, rely on the assumption that the computational power of a possible eavesdropper is limited. In fact, in principle, from the public key it would be possible to retrieve the private one, the task is however computationally challenging, and it is usually set such as no current technology could crack it in a reasonable time. This means that the security of public key encryption schemes does not rely only on the privacy of the private key but also on the limitation of the technology of a possible adversary.
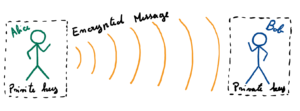
Cryptography however helps us once again. There exist in fact a protocol which requires only the privacy of a private key in order to be information theoretically secure. This protocol is known as the One Time Pad (see Figure 1) and works as follows. Two honest parties are in posses of a secret key k (a binary string of dimension n). One of the two can then encode a message m (of dimension n) just be applying an xor operation between the two strings and sending the resulting cypher-text c = k + m (modulo 2) through the channel. If k is private it will be known only by the two honest users and look completely random to any other listener of the communication. This fact is translated also for c, meaning that the cyphertext just look like a random string to anyone oblivious to the original key. This protocol seems to solve all the problem of the previous public key encryption scheme. However, there are two major constraints that must be respected for it to work.
- The key must be randomly generated and used only once (from this the name One Time Pad).
- The key must be in possession of the two honest parties.
Since each key can be used only once (a repeated key uses will breach some information to a carful adversary) new keys must be generated at each communication rounds. Randomness moreover must be ensured so that no one could foresee which key is produced. However, classical physics is deterministic meaning that knowing the initial conditions of a system would result into knowing the results of the whole process. Meaning, that we need another theory in order to guarantee the randomness of the generated key.
On the other hand, the key in the onetime pad should have the same length as the message and should be private once generated. This means that the two honest parties must exchange the key beforehand and keep it secret. But how can they share it if they are far from each other? Should they meet and exchange it before? If this was the case, they would as well exchange the message itself! Unfortunately, classical information theory does not help in this regard. We need a new physics in order to do it as in the previous case.
QUANTUM MECHANICS
Luckily, both issues stated before are solve using quantum mechanics. In fact, in this theory there are some very useful properties that help a lot the establishment of a secure and remote communication.
First, in quantum mechanics the result of some measurement (when the state prepared, and the measurement are not compatible) are intrinsically probabilistic. Meaning that no observer that abides to the laws of physics can foresee the results of these experiment, even if all initial conditions are known. By tailoring an experiment to work in this way we can generate genuine randomness that no third malicious party can have any information on.
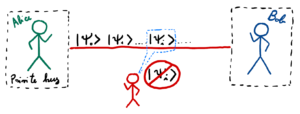
Second, certain sets of quantum states cannot be copied (see Figure 2). This property can be used for the broadcast of the key between two remote parties. In fact, as for the case before, any observer that is limited by physics cannot gain any information on the transmitted key. In fact, intuitively, since it cannot copy the state it has to measure it while the state it’s transmitted. This will cause the state to be altered and with a certain probability to produce a mistake at the receiver side. By measuring the amount of error occurred during transmission the two honest parties Alice and Bob can estimate how much information was stolen by the adversary, and by using a procedure called privacy amplification they can reduce this information to zero.
In the next sections we are going to investigate the recent developments in these two subjects that are known as Quantum Random Number Generation and Quantum Key Distribution, respectively.
QUANTUM RANDOM NUMBER GENERATORS
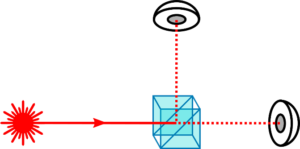
A simple example that can be given for quantum random number generator is the following: Let us imagine producing a simple photon (the most elementary part of the light) and send through a 50/50 beam splitter (see Figure 3). This element divides the incoming light in equal parts in the two outputs of the element. If a photon it is sent and two single photon detectors are used in order to collect the light at the outputs of the beam splitter, with a probability of 50% one or the other detector will click. This event is completely random and cannot be foreseen by anyone.
This simple device could in principle solve the problem of random generation of itself. However, in practice all the elements presented before could have some imperfections. Deterministic and reliable single photon sources are difficult to realize and not very performant (with respect to the bits generation rate need for secure communication). Often these sources are replaced with lasers that produced what is known as coherent states. Moreover, single photon detectors, even the best, do not have a unitary efficiency and are influenced by noise. All these imperfections must be considered, to estimate how many bits produced are due to quantum mechanical phenomena. This have the consequence of needing a precise characterization of the experiment.
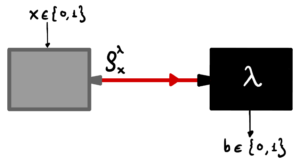
In the recent years a new approach has been developed. The idea is to have a quantum random number generator that is easy to implement, with good performance and that needs a minimum amount of characterization of the devices involved in the experiment. The idea comes originally from the work of J.B. Brask, A. Martin et al. Phys. Rev. Applied 7, 054018 (2017). This work implements a prepare and measure system where we would like to leave the measurement box completely untrusted (see Figure 4). The only assumption that would be made is on the input state, more precisely on the overlap of the two input states prepared . By bounding this quantity, we make the states not deterministically distinguishable, meaning that no physical measurement could distinguish between them with 100% precision. Either, we must allow for some errors, or we must allow the measurement device to give an inconclusive event from time to time. These spurious events must be random, in fact, if the were not they could be avoided leading to a better distinguishability and finally to a perfect discrimination of the two state which is a contradiction to the theory, meaning that errors and inconclusive events are intrinsically random. The discrimination efficiency can be measured by the input/output probabilities and this can be used to infer the amount of secure and quantum genuine bits that are produced by the experiment.
On this basis many recent experiments have been developed in the past few years, for example: D. Rusca, Phys. Rev. A 100, 062338 (2019) where the implementation of a Kennedy detector allowed for an implementation where the main assumption was just the average energy of the prepared states. On the same line in the work of D. Rusca, Appl. Phys. Lett. 116, 264004 (2020) the same protocol was implemented in a Homodyne detection scheme were the rate of 145.5 MHz genuinely quantum random bits was achieved.
QUANTUM KEY DISTRIBUTION
Now that we have shown a mean to produce genuinely random sequence of bits, we remain with the problem of how to distribute them to two remote trusted parties. This problem is the subject of studies of quantum key distribution (QKD). QKD has its origin with the first and most popular quantum cryptographic protocol of C. H. Bennet and G. Brassard of 1984, known as BB84. Since then many protocols have been developed and investigated. Moreover, a broad field of studies has been sprout trying to prove the security of all these protocols against all possible hacking attacks of third malicious parties.
Nevertheless, the BB84 remains one of the most used and studied protocols even today, given its simplicity of implementation and the good performance that it can achieve in transmitting secure secret strings of bits. For this reason, it is interesting to revise how it works and to see what kind of changes and improvements have been done on it during the years.
The protocol BB84 is what is known as a prepare and measure scheme. One of the two parties (Alice) prepares the sequence of random bits, it encodes it in some quantum states and sends it to the receiving party (Bob) that measures them. In BB84 Alice can chose between two non-compatible bases in the Hilbert space of dimension two, usually these bases are the Z basis (eigenstates and ) and the X basis (eigenstates and ) which eigenstates are a superposition of the previous basis. Intuitively this means that if a state of one basis is prepared and the measurement of the other basis it performs the result will be with 50% probability a mistake. The simplicity of the abstract protocol is undermined by the fact that it needs to exploit a Hilbert space of dimension two. If light is used to transmit the information, which is a very reasonable choice when tele-communications are considered, this is equivalent to prepare a single photon. Unfortunately, reliable deterministic single photon sources are not yet available. For this reason, currently most of experimental QKD implementations rely on the use of coherent states, easily produced by a laser source.
Coherent state BB84 have been one of the most interesting topics of interest for QKD in the past decades, and today it is one of the most preferred choice in commercial implementations. In order to achieve long distance security, however, another modulation must be added to the general scheme: the decoy-state method. In fact, by modulating the intensity of the coherent states prepared, it is possible to infer the fraction of secure single photon states exchanged by Alice and Bob and use once again the security proof for the original BB84.
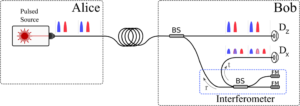
The most common decoy state BB84 uses four encoding states (using two orthogonal modes of light, e.g. polarization, time, phase) and three possible intensities for the decoy state modulation, where one is simply the vacuum. This means that in order to implement this protocol a total of nine different states must be prepared. In the past years however, it was discovered that it is not necessary to send all four encoding states of BB84 and only three are enough (see K. Tamaky Phys. Rev. A 90, 052314 (2014)). Moreover, in 2018 it was shown that a less popular decoy state method that uses only two intensity in the finite key regime was performing better than its more popular and complex counterpart (see D. Rusca Appl. Phys. Lett. 112, 171104 (2018)). Another recent simplification on this protocol was to allow Bob to discriminate unambiguously only three state out of the total four prepared usually (see D. Rusca Phys. Rev. A 98, 052336 (2018)). All these simplification of the original decoy-state BB84 allowed for the development of a recent time bin encoded QKD experiment (see Figure 5) that proved the secure transmission of a secret key over the distance of 421 km of ultra-low-loss fibre (see A. Boaron Phys. Rev. Lett. 121, 190502 (2018)).
CONCLUSION
In this brief document we tried to show how useful the properties of quantum mechanics are when used for secure communications. On one side the probabilistic nature of this theory allows for almost perfect random number generators which results no one could foresee. On the other side, quantum mechanics allows for private and secure key distribution for remotely position trusted parties, were any adversary abiding to the laws of physics cannot steal any information.
Thanks for your interest,
Davide Rusco






