Secure communication and quantum cryptography
Cryptography is, nowadays, a critically important part of our lives, even though we usually don’t notice it at all. All the conversations we have via email and instant messaging apps are encrypted, so are the messages exchanged during online bank transactions and e-commerce purchases. Even though the physical part of the message, the string of bits of which it is composed, is in principle available on the internet, its meaning is concealed, hidden behind some cryptographic scheme.
The internet is nowadays based on public key cryptographic schemes, whose security is based on the assumption that some specific mathematical problem is not efficiently solvable. If an eavesdropper, in the future, will find a way to efficiently solve such problem or will obtain an outstanding computational power, the security of our cryptographic scheme will be completely nullified. Quantum computers have the potential to achieve such ground-breaking results, posing a threat to today’s communication and economic systems.
Using the principles of quantum mechanics, several protocols resistant to such attacks have been devised and the field of quantum cryptography is in constant development. In the following we will focus on a specific area of quantum cryptography, namely, Quantum Key Distribution (QKD). Its greatest strength resides in the fact that keys expanded using QKD protocols can be proven to be secure in an information-theoretic manner, against and infinitely powerful eavesdropper limited only by the laws of quantum mechanics.
The standard QKD scenarios comprises two (or more) users, traditionally named Alice and Bob, who want to obtain a shared secure key. They can exchange quantum states (generally photons sent through optical fibres) through an insecure quantum channel and communicate over an authenticated classical channel. The eavesdropper (Eve) tries to obtain as much information as possible about the key, without being noticed, applying the most powerful attack she can. In the following we will state one of the main problems with the implementation of QKD and a possible path to alleviate it.
Satellite-based quantum communication
The first experimental implementation by Bennet and Brassard in the 80s and the subsequent record-breaking results proved that, while practically possible, QKD suffers some important limitations that are unknown in the field of classical cryptography. The most prominent of them is the intrinsic maximal scaling of the achievable key rate with the distance between the users. In public key encryption keys are shared, in a smart way, on the internet, so the key rate between two users is ultimately limited only by the bandwidth of the internet link, independently of the distance between them. The same holds if a direct communication link between the two is deployed: the classical signals that they share can be amplified during the propagation, making the data rate substantially independent of the distance. In quantum communication, on the other hand, any attempt to amplify a quantum signal will inevitable introduce disturbance, due to the  famous No-Cloning theorem. The result is that in standard QKD protocols the obtainable secret key rate scales linearly with the transmittance of the optical quantum link. If the photons encoding the quantum states are sent through optical fibres, like in the modern communication network, such scaling becomes exponential with the distance travelled, imposing severe limitations to the maximal distance between the users. A possible solution is to exploit optical links with more favourable loss-to-distance scaling, like free-space satellite-based links. The photons are in this case sent from a telescope on the orbiting satellite, through empty space and the atmosphere, before being collected by another satellite on the ground. The final proof of the feasibility of this technology was obtained by the Chinese Academy of Science with the satellite Micius, opening a path with giant scientific and economic potential.
famous No-Cloning theorem. The result is that in standard QKD protocols the obtainable secret key rate scales linearly with the transmittance of the optical quantum link. If the photons encoding the quantum states are sent through optical fibres, like in the modern communication network, such scaling becomes exponential with the distance travelled, imposing severe limitations to the maximal distance between the users. A possible solution is to exploit optical links with more favourable loss-to-distance scaling, like free-space satellite-based links. The photons are in this case sent from a telescope on the orbiting satellite, through empty space and the atmosphere, before being collected by another satellite on the ground. The final proof of the feasibility of this technology was obtained by the Chinese Academy of Science with the satellite Micius, opening a path with giant scientific and economic potential.
Influence of bad weather conditions and other environmental effects on satellite QKD
The advantageous scaling with the distance of satellite-based quantum links comes with some significant downsides.
Free-space optical links, like the satellite links introduced above, require a line-of-sight connection between the transmitter and the receiver, in stark contrast to the fibre-based implementation. This clearly implies that satellite QKD between orbit and ground can only be operated when the satellite is above the horizon and there are no buildings obstructing the line-of-sight. This also means that a single satellite can not ensure constant operation during the day, unless geostationary orbits are considered.
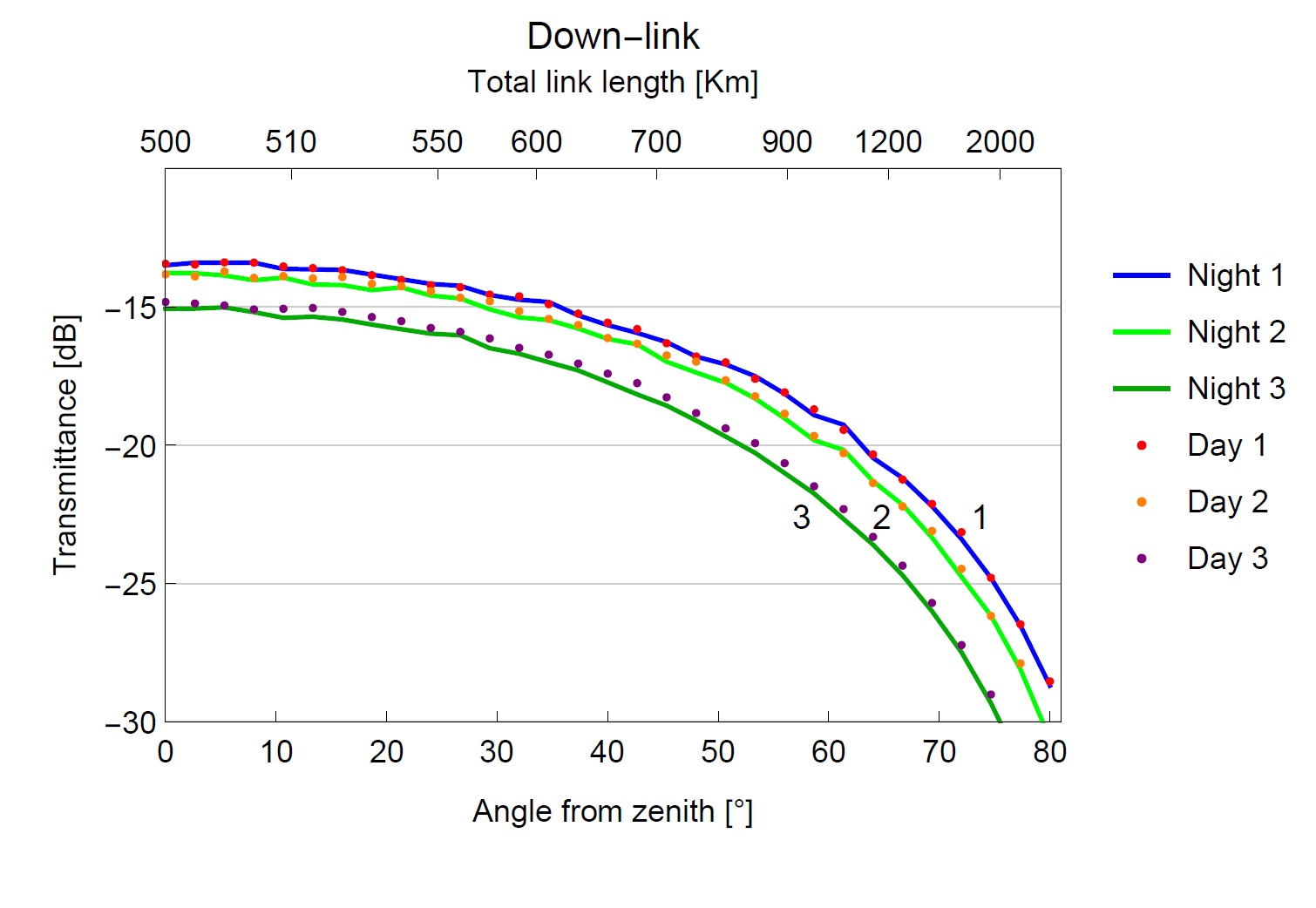 Even if clouds don’t completely obstruct the line-of-sight, bad weather conditions can still sensibly hinder the performance of satellite-based quantum links. Turbulence in the air and the presence of air droplets like haze or rain significantly change how the beams of light propagate in the atmosphere. The expected transmittance through the receiver telescope accordingly changes depending on the weather conditions, as shown in the figure (conditions get worse from 1 to 3, more results can be found here).
Even if clouds don’t completely obstruct the line-of-sight, bad weather conditions can still sensibly hinder the performance of satellite-based quantum links. Turbulence in the air and the presence of air droplets like haze or rain significantly change how the beams of light propagate in the atmosphere. The expected transmittance through the receiver telescope accordingly changes depending on the weather conditions, as shown in the figure (conditions get worse from 1 to 3, more results can be found here).
Satellite-based optical links are also prone to noise from environmental photons, since they use telescopes at the receiver that can collect stray light together with the signal. This effects can generally be counteracted using temporal, spatial and spectral filtering.
The importance of untrusted nodes
All the information we send on the internet, as already discussed, is safely encrypted with a cryptographic key to protect it from any unauthorized eavesdropper. Now, imagine that the key used for encryption is available to someone or to some company, e.g., the provider of the key. It means that that particular individual can read your information as plain text and make it public. In some cases, there are some barriers that make this problem not worrying, for example, the provider of the key doesn’t want to damage his trustworthiness. We cannot always count on this, though.
Trusted-node quantum networks is a “cheap” solution to achieve long distance quantum communication. In the QKD case, the distance between Alice and Bob is divided into elementary links of shorter length. The keys are exchanged in parallel between the adjacent nodes and then, by doing simple logical operations on the keys and communicating publicly the result, Alice and Bob can share a common key without leaking information to Eve. The problem with this approach is that the intermediate nodes, that do the operations on the keys, will also end up knowing the key. This means that the nodes need to be trusted by the parties and this can be especially tricky when, trying to achieve intercontinental distances, the nodes are in different countries. So, a solution without intermediate trusted nodes is demanded.
Quantum repeaters in space
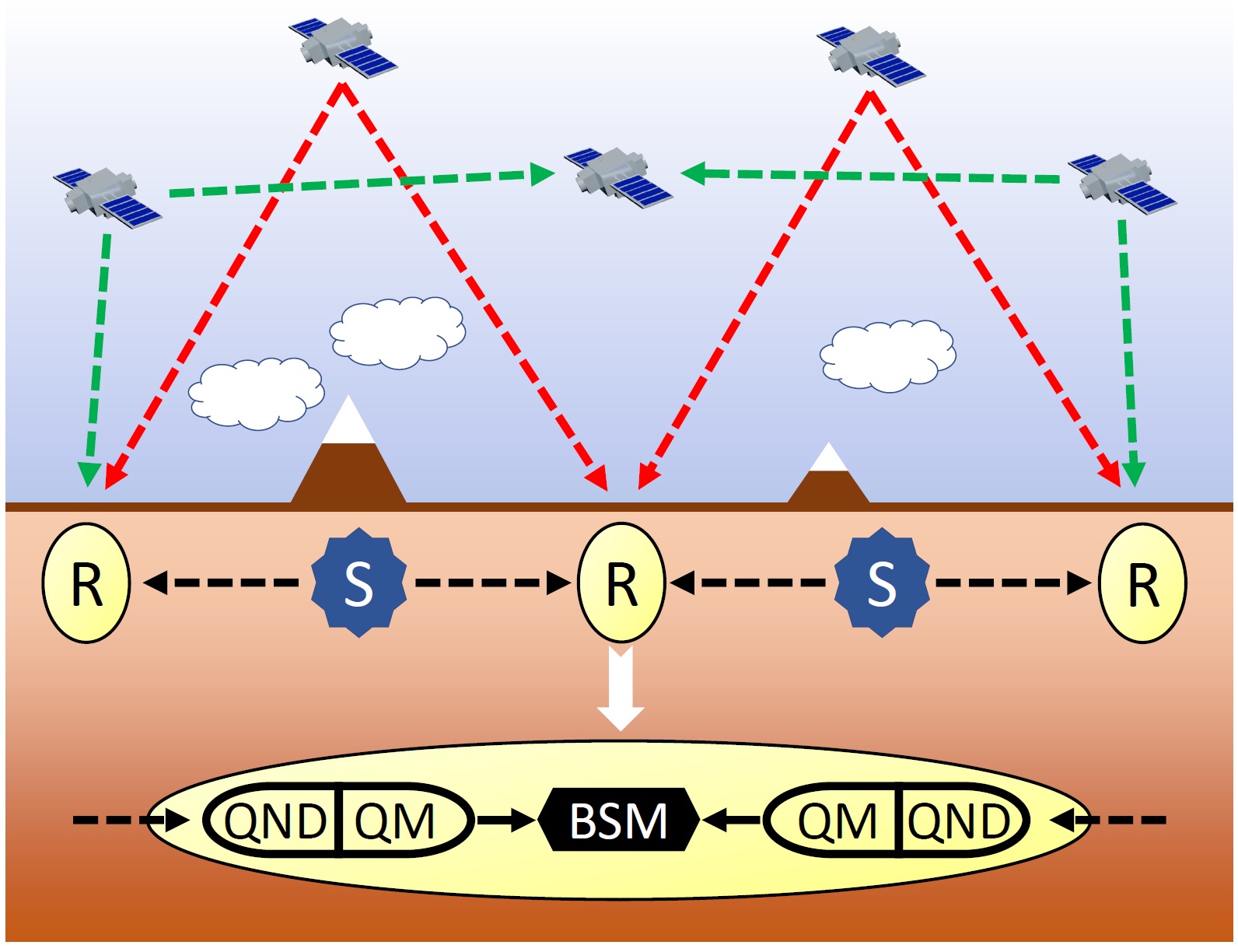
Quantum repeaters allow to build untrusted-node quantum networks. As before, the total link is divided into several shorter elementary links (middle section of the figure). 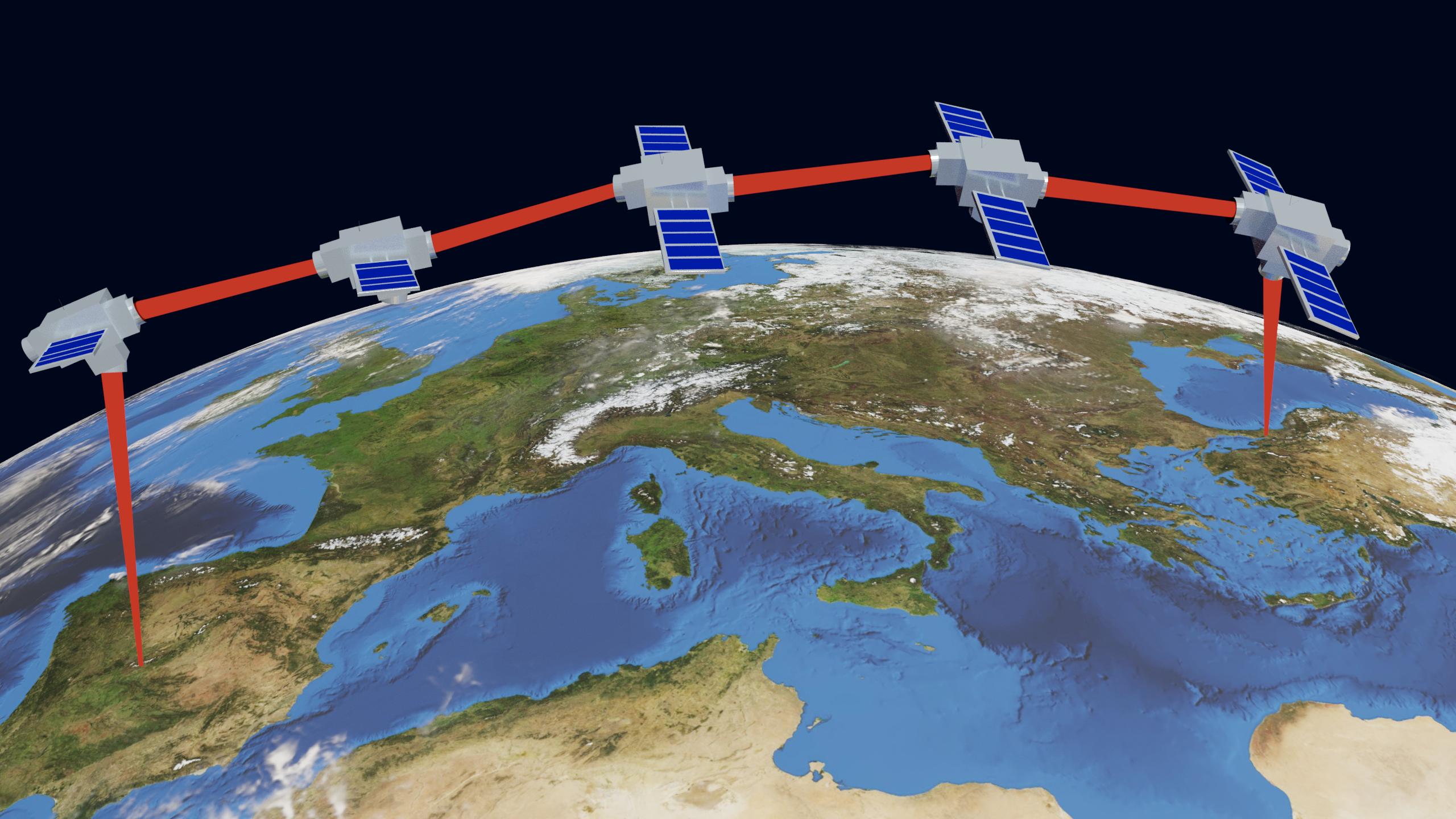 Entanglement sources (S) are put in the middle point of the links and quantum repeaters(R) at the junctions. Performing entanglement swapping at the repeater stations in a hierarchical way allows to enlarge the range of the quantum correlations, until we reach the end points of the chain. The shared entanglement can then be used to perform quantum communication protocols without trusting the middle nodes.
Entanglement sources (S) are put in the middle point of the links and quantum repeaters(R) at the junctions. Performing entanglement swapping at the repeater stations in a hierarchical way allows to enlarge the range of the quantum correlations, until we reach the end points of the chain. The shared entanglement can then be used to perform quantum communication protocols without trusting the middle nodes.
When this technology is composed with the use of satellite-based links, it allows to bridge global distances using a small number of intermediate nodes (details here). One can even imagine a configuration like the one in the figure, in which all the components of the chain are orbiting in a cohesive 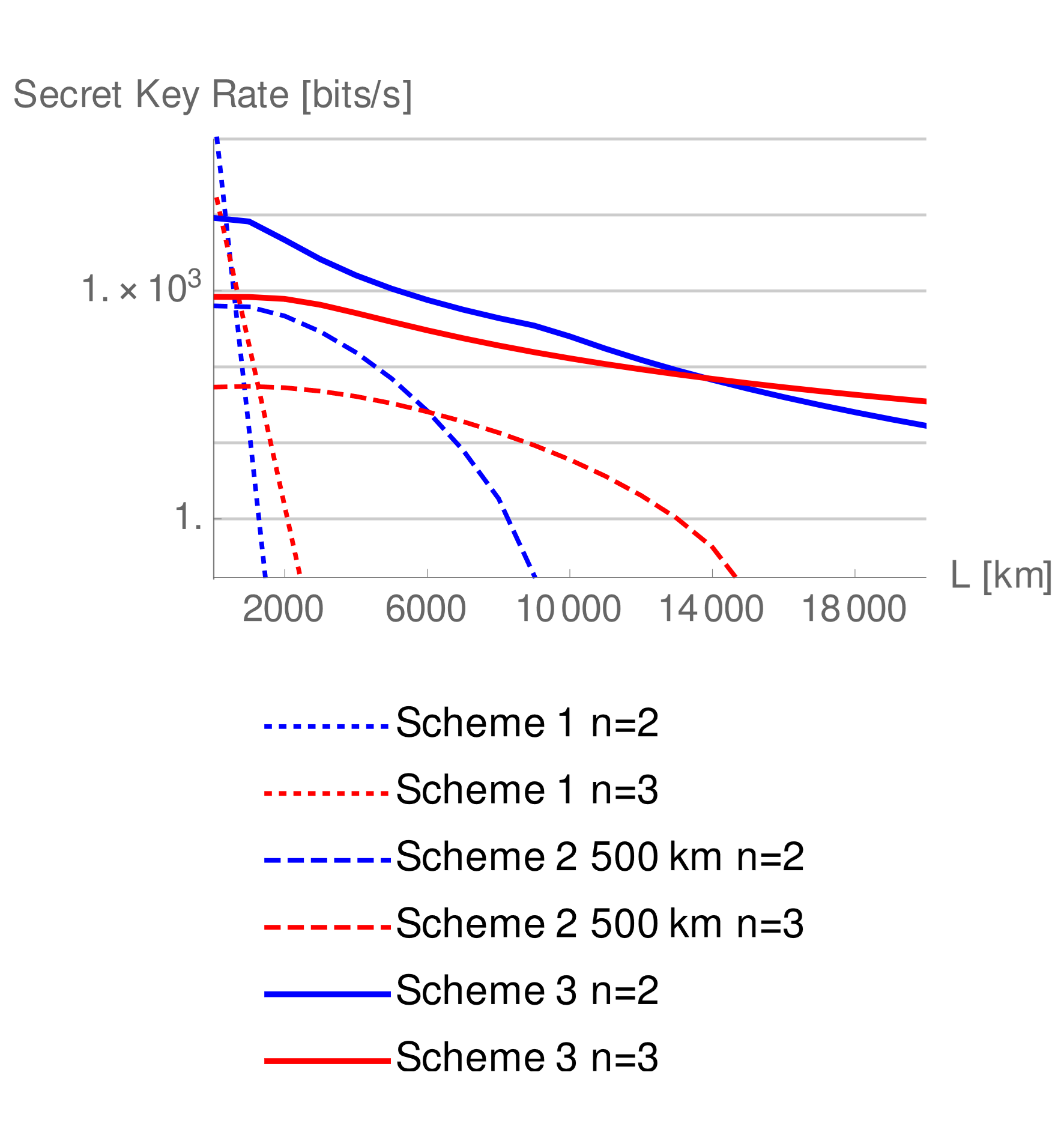 manner and only the end users are on the ground. We can see the result of simulations in the graph beside. The scheme with orbiting quantum repeaters (thick solid lines) ensures a positive key rate even at a distance equal to half the Earth’s equator, while the implementation in fibre (dotted lines) fails already around 2000km.
manner and only the end users are on the ground. We can see the result of simulations in the graph beside. The scheme with orbiting quantum repeaters (thick solid lines) ensures a positive key rate even at a distance equal to half the Earth’s equator, while the implementation in fibre (dotted lines) fails already around 2000km.
Entanglement distribution: beyond cryptography
The ability to distribute entanglement over very long distances will open the path for many more useful quantum-enabled protocols, on top of secure communication. One example is represented by cloud-based quantum computation. Many companies world-wide are investing billions of dollars to develop quantum computers and get to the point where they will be actually useful on practical problems. However, such devices will not come into our houses in the near future. As we do nowadays with supercomputers and servers, these quantum processors will be few and bought by companies or computing centres. The users will access their capabilities as a cloud service, using either classical or simple quantum inputs to impart commands to the quantum computer and then receive the output of the correspondent computation. In this context entanglement is a precious resource, for example it can be used to teleport quantum states from the user to the server and back. Another interesting application of long distance entangled pairs is quantum metrology. This field comprises the protocols that, using inherently quantum properties like entanglement, measure some physical quantity with higher precision and resolution than standard classical methods. An interesting example is given here, where the authors describe a protocol to achieve high resolution interferometric measurements for astronomical observations using entangled pairs distributed between the observatories.
Quantum technologies are in constant development and the QCALL network is proud of the contribution it gave to the field. Stay tuned for more interesting stories!